Cybersecurity has been called the greatest threat to every company in the world. As the world becomes increasingly autonomous and tech-driven, this threat will only continue to grow. And if addressing the threat itself was not enough, companies will also need to comply with an increasingly complex set of data protection rules and regulations.
All of these require that companies have access to a digitally equipped pool of talent. So, this is where EIT Digital comes into play. With our Cybersecurity master's programme, you will not only build the skills to compete for the often high-paying jobs, but you will also gain the confidence to help drive the transformation toward a safer, more secure digital world.
Key benefits
The diversified master's programme is designed to give you a general overview of the role that cybersecurity plays in creating a safe and inclusive digital society. It also equips you with practical skills in ethical hacking, blockchain technologies, and quantum cryptography.
This comprehensive approach to cybersecurity ensures that you are well-positioned to secure such roles as:
- Cybersecurity consultant
- Security analyst
- Information security architect
- Cybersecurity specialist
- Computer forensics expert
- Privacy-by-design consultant
- Security auditor
To enhance your learning, the programme also includes an opportunity to get real-world experience working in some of Europe’s leading coworking centres and innovation incubators. This is a one-of-a-kind chance to apply your new skills and knowledge towards solving actual cybersecurity challenges. You will also be able to augment your cybersecurity skills by taking tailored courses in innovation and entrepreneurship.
Is this programme for me?
Our Cybersecurity Master’s programme is open to applicants with either a Bachelor of Science degree or who are in their final year of study in:
- Computer Science
- Information Systems
- Mathematics
- Electrical Engineering
Applicants with reasonable knowledge of the fundamentals of computing and information sciences and technologies may also be considered. In some circumstances, relevant work experience may compensate for a lack of relevant degree. If you have such work experience, make sure to include it in your letter of motivation.
How is the programme structured?
All EIT Digital Master School programmes follow the same scheme:
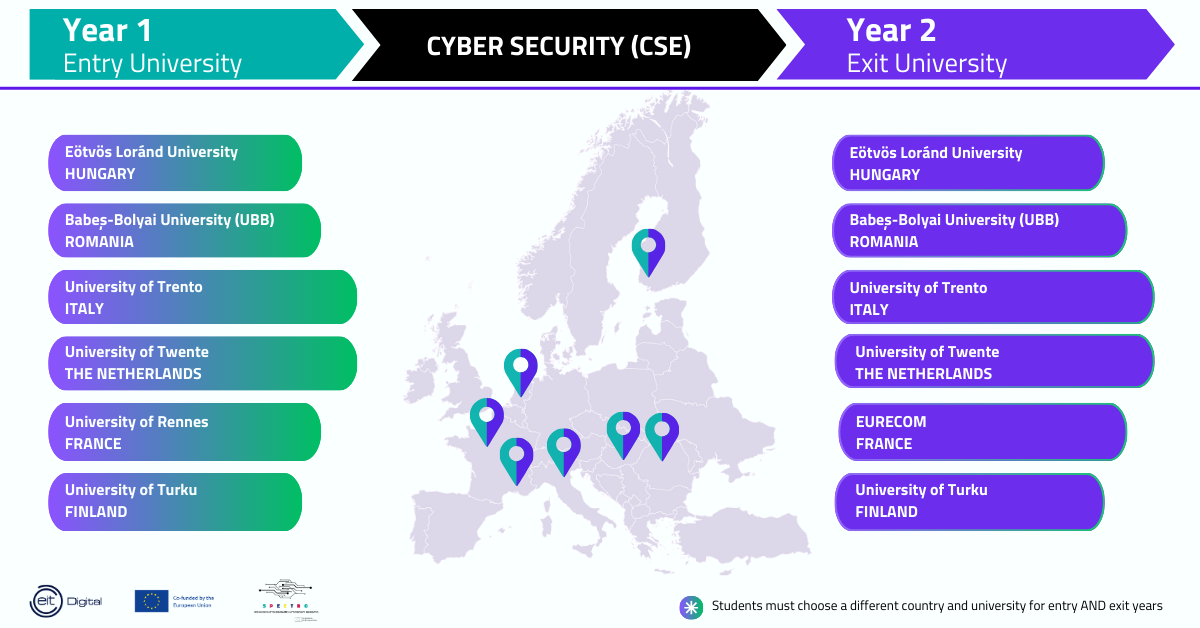
- Students study one year at an ‘entry’ university and one year at an ‘exit’ university.
- The first year is similar at all entry points, with a focus on basic courses that lay the foundation for the chosen technical programme. Students are introduced to business and management during this first year. During the second semester, a design project is combined with business development exercises to demonstrate how technology can be transformed into a successful business with optional elective courses. Students are taught how to prepare and present a convincing business plan.
- In between the first year and the second year, students participate in the EIT Digital 2-week Summer School programme that addresses business opportunities within a socially relevant theme.
- The second year offers a specialisation and a graduation project. The graduation project includes an internship at a company or a research institute and cumulates with a Master thesis having a strong innovation and entrepreneurship dimension.
- Graduates receive degrees from the two universities and a certificate awarded by the European Institute of Innovation and Technology.
To learn more about the I&E minor please click here.
Scholarships
With the support of the SPECTRO project, EIT Digital provides for three types of scholarships:
- Scholarships of Excellence - Full tuition fee waiver and monthly allowance (based on average living costs in the study country)
- Full tuition fee waiver
- Half tuition fee waiver
Scholarships are only available to EU Member States nationals (including overseas countries and territories (OCTs) and nationals from listed EEA countries and countries associated to the Digital Europe Programme.
You apply for scholarships during the application process in the application portal.
Please note that besides the scholarships offered by EIT Digital, our students may also be eligible for other scholarships, grants or financial aid offered by our partner universities. Check all of our Scholarships and Additional Financing Options.
The funding scheme is also advertised on the EU Funding & Tenders portal